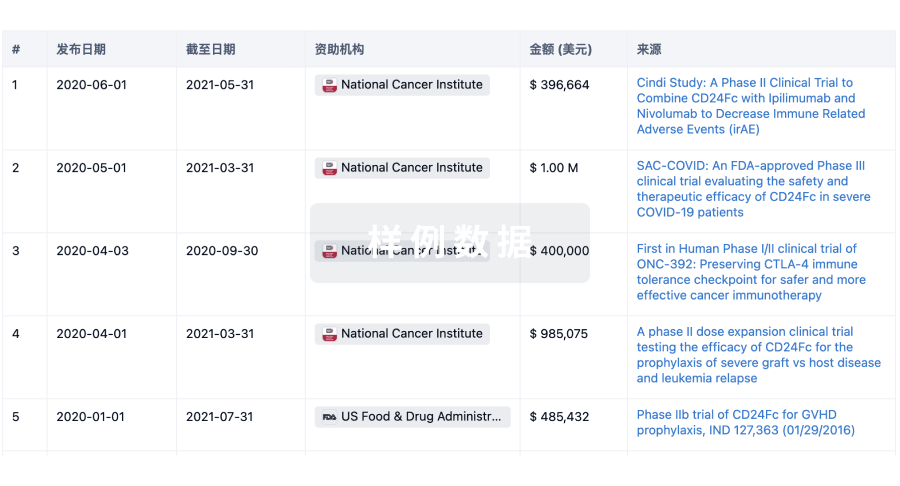
Cloud computing has dramatically changed service deployment patterns. In thiswork, we analyze how attackers identify and target cloud services in contrastto traditional enterprise networks and network telescopes. Using a diverse setof cloud honeypots in 5~providers and 23~countries as well as 2~educationalnetworks and 1~network telescope, we analyze how IP address assignment,geography, network, and service-port selection, influence what services aretargeted in the cloud. We find that scanners that target cloud compute areselective: they avoid scanning networks without legitimate services and theydiscriminate between geographic regions. Further, attackers mineInternet-service search engines to find exploitable services and, in somecases, they avoid targeting IANA-assigned protocols, causing researchers tomisclassify at least 15\% of traffic on select ports. Based on our results, wederive recommendations for researchers and operators.